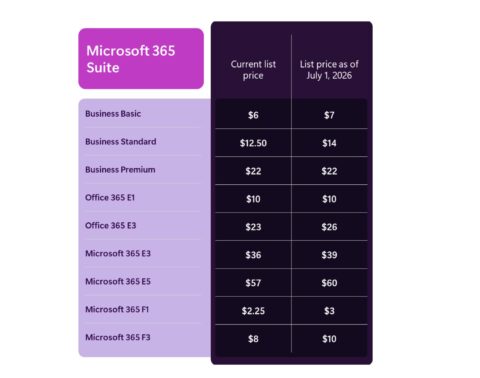
Updated: May 23, 2024 (May 22, 2024)
BlogMicrosoft clarifies (a bit) its MFA for 'all' Azure users edict
On May 14, Microsoft posted a blog which stated that multifactor authentication (MFA) would be required for “all” Azure users starting in July 2024. The post, which was very light on details, did highlight why (Do security!) Microsoft is making this change, but failed to provide anything about possible exemptions, implementation and other important information.
Deep in the rapidly growing number of comments on the blog post, Naj Shahid, Principal Product Manager for Azure, added a few of the missing details about the edict.
Shahid explained that Microsoft won’t actually require all Azure users to use MFA.
“Students, guest users and other end-users will only be affected if they are signing into Azure portal, CLI, PowerShell or Terraform to administer Azure resources. This enforcement policy does not extend to apps, websites or services hosted on Azure. The authentication policy for those will still be controlled by the app, website or service owners,” Shahid noted.
In addition, service accounts, managed identities, workload identities and other token-based automation accounts will be excluded from the MFA requirement, he said. For cases where no workaround is available, there will be an exception process, which Microsoft will detail via official notifications.
Starting in July, Microsoft will be gradually enforcing the MFA sign-in policy for portal. Once that’s completed, a similar gradual rollout will kick off for CLI, PowerShell and Terraform, Shahid said. Each step of the way, Microsoft will send customers information through emails and notifications, to let them know what is happening when.
“We understand the impact this enforcement could have on automated scripts using user identities and thus are prioritizing enforcement for Azure portal to provide additional time to adapt if needed,” he added.
Microsoft’s guidance is for admins not to wait to set up MFA with the MFA Wizard for Microsoft Entra. Entra ID supports various MFA methods, such as the Microsoft Authenticator app, SMS, voice call, and hardware tokens. Admins can also use Entra ID Conditional Access policies to tune when MFA is required based on signals such as the user’s location, device, role, or risk level, as Microsoft noted in the original blog post.
“Microsoft recommends examining which Entra IDs are used with dev ops and API access to Azure Resource Manager. As needed, learn how to replace user identities with service principals and managed identities,” Shahid advised.
Related Resources
May 14: Microsoft will require MFA for all Azure users
Customers Must Prepare for MFA Unification (Directions members only)