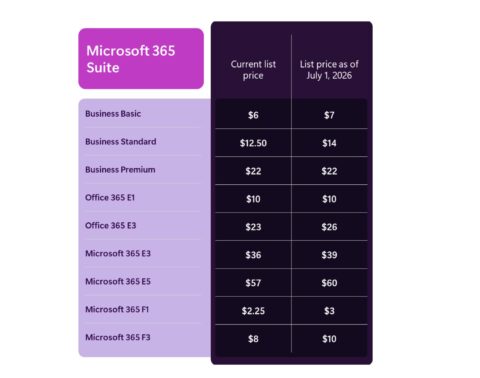
Updated: July 4, 2023 (June 19, 2023)
BlogMicrosoft admits early June DDoS attacks impacted its cloud services (and maybe yours, as well)

After disruptions to its Office, Outlook, OneDrive and Azure services from June 5 to June 9, Microsoft acknowledged via a blog post late last week that distributed denial-of-service (DDoS) attacks from threat actor “Storm-1359” were to blame. The multi-day incident no doubt will raise a lot of questions among Microsoft customers, especially enterprise customers who are increasingly reliant on Microsoft to power their business operations.
On the plus side, Microsoft officials said they had seen no evidence that customer data was accessed or compromised as part of the DDoS attacks. However, the quiet way Microsoft disclosed this information doesn’t inspire confidence.
The company opted to post about its findings late in the day on June 16, the Friday before what is a long holiday weekend for many in the U.S. (In the media, we call this a “Friday news dump.”) As security expert (and former Microsoft employee) Kevin Beaumont noted on Twitter, they also didn’t point to the blog on their usual social channels or name Azure or Microsoft 365 as being affected, while both appeared to be.
When various news outlets asked Microsoft earlier this month why services like the Azure portal were down, the “official” answer was an unusual spike in traffic. On Friday, however, a Microsoft spokesperson said in response to an AP request for comment that the group called “Anonymous Sudan” was behind the attacks.
Microsoft’s blog post about the attacks, entitled “Microsoft Response to Layer 7 Distributed Denial of Service (DDoS) Attacks,” noted that the early June DDoS incidents were likely due to a collection of botnets and tools that allowed Storm-1359 to launch attacks from multiple cloud services and open proxy infrastructures. The types of attacks included HTTP(S) flood attacks, cache bypasses and “Slowloris,” or attacks which can cause a web server to keep a connection open longer than it should be. The intent of the attacks “appears to be focused on disruption and publicity,” officials said.
As the Azure Firewall Turns
Microsoft is recommending customers use Layer 7 protection services such as Azure Web Application Firewall, which is available with Azure Front Door and Azure Application Gateway, to protect web applications. Its blog post unsurprisingly didn’t specify what Microsoft itself did and is doing to try to stop these kinds of attacks.
Many customers assume once they commit to Azure or Microsoft 365 that Microsoft will keep them safe (or at least safer than they can keep themselves) from attacks, given the company’s sizeable investments in security. Additionally, customers may have a false expectation that cloud services like Azure, Microsoft 365, and similar offerings can continue to deliver resilient services for customers under all conditions and simply absorb large-scale attacks like this. Microsoft does continue to make adjustments to try to stay ahead of all kinds of bad actors. But these kinds of DDoS attacks highlight that even a cloud vendor with vast resources is still vulnerable, and its customers are, in turn.
“Although Microsoft has focused on Azure Active Directory (AAD) resilience a lot in the past several years, the reality is that key Azure services like AAD are at the core of all Microsoft services. And even when designed for high resilience, malicious attacks like this can take down large chunks of services for customers around the world,” said Directions on Microsoft analyst Wes Miller.
Microsoft was scheduled to hold a press event focused on its Entra security and identity products and strategy on June 20, but on Friday abruptly announced the virtual event was postponed until July 11. A coincidence? I’m doubtful. I also don’t think it’s a coincidence that my increasingly growing problem with spam flooding my Outlook and Outlook.com accounts almost entirely has tapered off since Microsoft assumedly made changes to battle these DDoS attacks…. but I digress. (Or do I?)