Updated: April 8, 2024 (July 19, 2023)
BlogMicrosoft to broaden access to cloud security logs following China e-mail hack

A week after disclosing that a China-based hacking group (“Storm-0558”) infiltrated some individual and government Outlook email accounts for a month, Microsoft announced it will broaden access to security logs to include Microsoft 365 customers who are not paying for pricey premium security services.
“In the coming months,” Microsoft plans to broaden access to cloud security logs for no additional cost, according to a blog post the company published on July 19. While this transition happens, Microsoft is advising customers to use Microsoft Purview Audit in order to see more types of cloud log data.
Log data doesn’t prevent customers from getting hacked, but it does give them a way to try to proactively respond to issues. Some customers and company watchers believe log data should not be considered a premium feature, as it is fundamental to security. But Microsoft is not going as far as to make logging data free for all business customers.
Microsoft officials said they decided on the newly announced strategy “in close coordination with” government and commercial customers and the Cybersecurity and Infrastructure Security Agency.
The company is going to enable Purview Audit Standard customers to see detailed logs of e-mail access, along with more than 30 other types of log data that previously were only available to Purview Audit Premium subscribers. Microsoft also will increase the default retention period for Audit Standard customers from 90 days to 180 days.
Under the revised plan, Purview Audit Premium customers with E5/G5 licenses still will maintain more audit logging access. This includes the ability to use Audit log search in the Purview compliance portal and the Office 365 Management Activity programming interface; longer default retention periods; and automation support for importing log data into other analytics tools.
Restoring trust
“In some ways Microsoft finds itself back where it has a trustworthy computing problem,” said Directions on Microsoft analyst Michael Cherry. “Its latest actions surrounding an incident by a sophisticated bad actor raises serious doubts. Can Microsoft Azure and Office 365 customers count on these services being secure by design, secure by default, and secure by deployment, as well as providing fully transparent communications about any vulnerabilities and steps companies must take to mitigate exposure? If Microsoft partitions its security services and information to entice customers to pay more for better or for full security, then is the answer no—maybe they shouldn’t be trusted? Full access to logs, and the tools to spot problems in the myriad of log entries would be a good starting point to begin restoring some trust.”
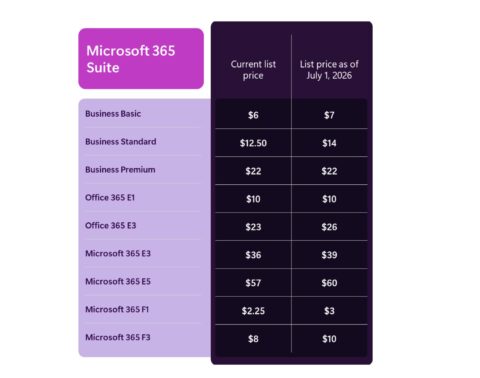
In the case of the recent China e-mail hack, logging information that would have allowed detection of the incident was only available to those Microsoft 365 customers who purchased the premium E5 plan. Those running E3 were unable to see the required logging information.
As The Wall Street Journal noted, executives with the U.S. federal government, including the State Department and Commerce Department, were victims of the attack, leading some government officials to call for Microsoft to make cloud logs more widely available.
Update (September 11) On September 6, Microsoft posted more information about how the bad actor Storm-0558 acquired a Microsoft Account (MSA) consumer key to get enterprise access to business/government accounts. But its technical investigation findings are unlikely to ease business customers’ worries.
“Microsoft is telling customers that they should examine logs between April 2021 and June 2023 to make sure they weren’t sideswiped too. But only customers with M365 E5 and Advanced Audit and who had configured logs correctly before April 2021 (or had started sending them all out to Splunk or Sentinel back in 2021) would even have all those logs to peruse,” noted Directions on Microsoft analyst Wes Miller. “E3 customers wouldn’t even be able to look back before June at this point. E5 customers would be able to look back to September 2022. “
Related Resources
Expanding cloud logging to give customers deeper security visibility
Microsoft’s latest email hack: M365 E3 subscribers beware
CISA: When Tech Vendors Make Key Logging Info Available for Free, Everyone Wins